Types of VPNs and Their Security Protocols

Table of Content
VPN stands for Virtual Private Network. In today’s digital era, we all use the Internet to make online transactions, buy products online, and transfer money from one person to another, and much more. To keep your online activities secured from hackers and viruses, you must use a reliable VPN service on your system. Here, we have listed down the types of VPNs and what protocols do they offer to secure your Internet connections. Let’s check them out!
Types of Virtual Private Networks
In general, VPNs can be categorized into two different types, remote access VPN and site-to-site VPN. Both types have their own limitations and advantages and they provide different securities to your systems and other connected devices. Let’s get into the details!
-
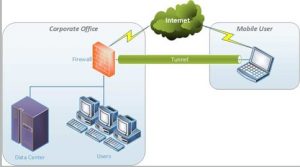
Remote Access VPN
This is the most common type of VPN which is highly used by the home-users and small enterprises. It allows users to connect to the different systems and explore all the features and resources with no limitations. You can connect to multiple devices and can use the Internet from unknown sources remotely. It doesn’t ask for any type of wired connection or any particular device to connect and explore its services.
-
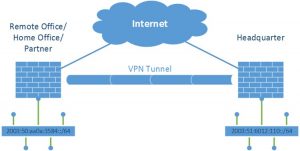
Site to Site VPN
Generally, unlike remote access, VPN and VPN are recommended for big enterprises but Big companies with a number of departments and hundreds of employees use this VPN to keep everyone safe over the Internet.
You can establish a connection within your company with the Intranet connection or can connect it with the other company using the extranet connection. Depending on your requirements, you can use a suitable connection option.
Follow VPN-related news to keep yourself up to date with the different types of VPNs and their latest security technologies. Now let’s understand the different security protocols used by the VPN providers to safeguard your connected devices and PC systems.
VPN Security Protocols
-
Open VPN
Open VPN is the most common security protocol used by VPN providers for point-to-point connections between the systems. It works with the SSL and TLS security protocols.
-
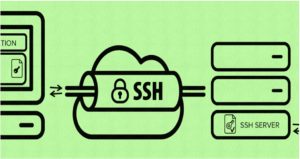
SSH
SSH-Secure Shell-which is a more advanced and secured protocol compared to the Open VPN. It provides a secure tunnel to let the data pass through it and the tunnel encrypts your data and this way, it provides an extra layer of security to your system and the connections.
-
Point-to-Point Tunnel Protocol
PPTP stands for point-to-point tunnel protocol and PPTP provides a tunnel to encrypt the data with the packages. It provides security to your data with advanced point-to-point and encryption techniques and PPTP protocol is widely used by the Mac and Linux systems due to its advanced security.

-
L2TP
L2TP is also known as a layer 2 security protocol in the technical term and Layer 2 transfer protocol combines with the other security protocol to safeguard your data and connections. This security protocol creates a tunnel between the data transfer of two systems and with the use of other protocols. And it encrypts all the data transfer through the tunnel. This way, it provides an additional layer of security.
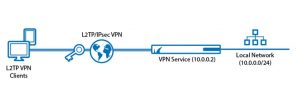
L2TP is widely used by communication platforms and devices to make secure voice calls and video calls etc.
-
IPsec
IPsec stands for Internet Protocol Security. This protocol is used to secure internet communication between the connected devices but this protocol is yet another commonly used protocol by the VPN providers to secure the connection by encrypting the data packets in bulk instead of encryption single files. IPsec works with two different security modes, transport mode, and tunneling mode.
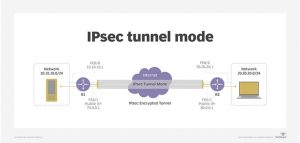
IPsec is widely used by security agencies to keep things private and protected. This protocol can be combined with other security protocols to improve the security level between the systems.
-
SSL and TLS
SSL and TLS security protocols are there for those for specific Internet-related tasks. These security protocols allow users to have access to a limited number of applications and files over the Internet.
SSL is highly used by websites to offer a secure path to users. SSL adds up an additional security layer to your website with HTTP but It is not secured if you see the website with just HTTP.