INTERNET
-
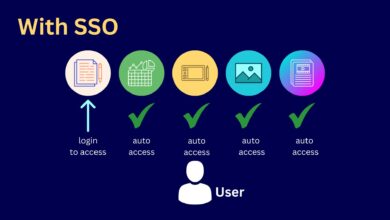
SSO: Simplifying Access to Multiple Applications
Single Sign-On (SSO) is a technology that allows users to authenticate themselves once and gain access to multiple applications and…
Read More » -

Microsoft Consulting Services: Expert Solutions for Your Business
Microsoft Consulting Services is a branch of Microsoft that provides consulting services to businesses and organizations. The goal of these…
Read More » -

The Science of Flower Colors: Exploring Pigments and Perception
Ever paused to ponder the science behind these vibrant hues or the profound impact they have on both our psyche…
Read More » -

Your Comprehensive Guide to Microsoft Consulting Services
The corporate world is becoming increasingly tech-driven, with companies relying on digital tools more than ever for improved efficiency, productivity,…
Read More » -

Mastering Trading Skills: The Pros of Bubinga’s Demo Trading Account
In the ever-evolving landscape of financial markets, success often hinges on the ability to make informed decisions, execute strategies effectively,…
Read More » -

Trendzguruji.me Cyber: Understanding the Latest Online Threats
Trendzguruji.me Cyber is a popular website that provides tech enthusiasts with the latest news, reviews, and updates on cybersecurity. The…
Read More » -
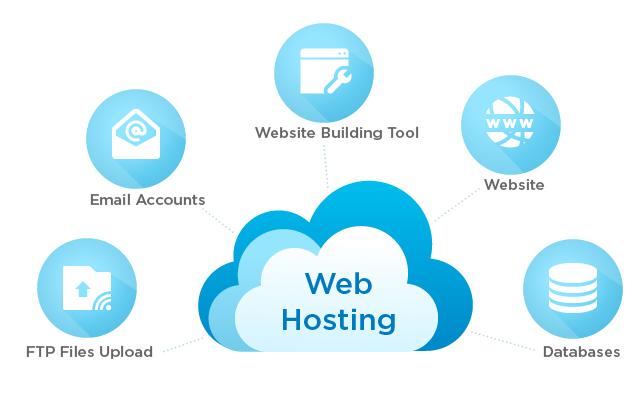
Guides Before Choosing the Right Web Hosting for Your Business
Web hosting services are an essential component of the internet, allowing individuals and businesses to create and maintain websites. A…
Read More » -
Putlocker: Top 15 Alternatives And Best Mirror Sites For Fans
Putlocker is a popular website wherein cinephiles enjoy most of their time downloading or want to watch free movies online.…
Read More » -
KissCartoon: Top 15 Alternatives To Watch Favorite Cartoon series
KissCartoon, now known as KimCartoon, is a safe free online cartoon website that streams videos of many genres. Online viewers…
Read More » -

Top 10 Craigslist Alternatives For Classified Ads
Craigslist is an advertising website that allows users to sell their debris online. The best aspect is that you may…
Read More »
